.png) |
| Computer Network Components |
A computer network consists of various components that work together to enable communication and data exchange between connected devices. Here's an in-depth explanation of some key components:
A. Network Devices:
Network devices are physical or virtual entities that facilitate communication within a network. Common devices include routers, switches, hubs, and access points:
1. Modems and Routers:
Modems and routers play crucial roles in connecting a local network to the internet.
a. Modem (Modulator-Demodulator):
Modems convert digital data from computers into analog signals for transmission over telephone lines or cable systems. They also demodulate incoming analog signals back into digital data.
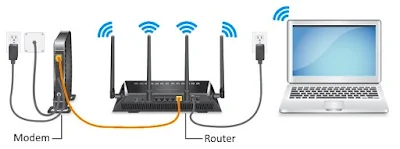
b. Router:

Routers direct data traffic between a local network and the internet. They use routing tables and protocols to determine the best path for data packets to reach their destination. Routers connect different networks and facilitate the exchange of data between them. They operate at the network layer (Layer 3) of the OSI model and make decisions based on IP addresses.
2. Switch:
Switches operate at the data link layer (Layer 2) and are responsible for forwarding data within the same network. They use MAC addresses to determine the destination of data packets.
3. Hub:
Hubs connect multiple devices within a network. Unlike switches, hubs do not filter data based on MAC addresses, causing all connected devices to receive the transmitted data.
4. Access Point:
Access points (APs) provide wireless connectivity to devices in a local area network (LAN). They allow devices to connect to the network using Wi-Fi.
B. Networking Cables:
Networking cables are the physical medium through which data is transmitted in a network. Different types of cables are used, depending on the network architecture and requirements.
1. Ethernet Cables:
Ethernet cables are commonly used in wired networks. They come in various categories (e.g., Cat5e, Cat6) and support different data transfer speeds.
2. Fiber Optic Cables:
Fiber optic cables use light signals to transmit data, offering high-speed and long-distance connectivity. They are resistant to electromagnetic interference and suitable for high-bandwidth applications.
3. Coaxial Cables:
Coaxial cables are often used in cable television networks. They consist of a copper core surrounded by insulating layers, providing reliable data transmission.
C. Network Adapters:
1. Network adapters, also known as network interface cards (NICs):
It enable devices to connect to a network. They can be integrated into a device's motherboard or added externally.
2. Wireless Network Adapters:
Wireless NICs allow devices to connect to Wi-Fi networks. They enable laptops, smartphones, and other devices to communicate without physical cables.
3. Ethernet Network Adapters
Ethernet NICs facilitate wired connections, connecting devices to a network using Ethernet cables. They are common in desktop computers and servers.
D. Networking Protocols:
Protocols are a set of rules that govern how data is transmitted and received in a network. They define the format, timing, and sequencing of data packets.
1. TCP/IP (Transmission Control Protocol/Internet Protocol):
TCP/IP is the foundational protocol suite of the internet. It ensures reliable and ordered delivery of data packets.
2. HTTP/HTTPS (Hypertext Transfer Protocol/Secure):
HTTP is used for web communication, while HTTPS adds a layer of security through encryption. They define how web browsers and servers exchange information.
3. DNS (Domain Name System):
DNS translates human-readable domain names into IP addresses. It enables users to access websites using easily memorable names.
E. Network Security Devices:
Network security devices protect the integrity and confidentiality of data within a network:
1. Firewall:
Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules. They act as a barrier between a trusted internal network and untrusted external networks.
2. Intrusion Detection System (IDS) / Intrusion Prevention System (IPS):
IDS monitors network or system activities for malicious actions or security policy violations, while IPS takes preventive actions to block or mitigate detected threats.
3. VPN (Virtual Private Network):
VPNs provide secure communication over an untrusted network, such as the internet. They encrypt data to ensure confidentiality and privacy.
F. Servers:
Servers are powerful computers designed to provide services and resources to other devices on the network.
1. File Server:
File servers store and manage files that can be accessed by other devices on the network. They facilitate centralized data storage.
2. Web Server:
Web servers host and serve website content to users over the internet. They respond to requests from web browsers and deliver web pages.
3. Database Server:
Database servers manage and provide access to databases. They handle data storage, retrieval, and management for various applications.
These components collectively form the infrastructure of a computer network, enabling efficient communication, resource sharing, and data exchange among connected devices. Understanding the roles of each component is crucial for designing, implementing, and maintaining robust and secure networks.
Let's explore additional components and aspects of computer networks in more detail:
A. Network Operating Systems:
Network operating systems manage and coordinate network resources and services. They provide a platform for running applications, file sharing, and user authentication.
Windows Server:Windows Server is a network operating system developed by Microsoft. It facilitates centralized management, file sharing, user authentication, and other network-related tasks.
Linux-based Servers:Various Linux distributions, such as Ubuntu Server and CentOS, serve as network operating systems. They are widely used for their stability, security, and versatility in server environments.
B. Network Topologies:
Network topology refers to the physical or logical layout of devices in a network.
Bus Topology:Devices are connected to a central cable (bus). Data travels along the bus, and each device receives all transmitted data, but only the intended recipient processes it.
Star Topology:Devices are connected to a central hub or switch. All data traffic passes through the central hub, allowing for easy management and troubleshooting.
Ring Topology:Devices are connected in a closed-loop, with each device having exactly two neighbors for communication. Data travels in one direction around the ring.
Mesh Topology:Devices are interconnected, forming multiple paths for data to travel. Mesh topologies provide redundancy, ensuring continued connectivity even if one link fails.
C. Network Services:
Network services are applications or processes that provide specific functionalities within a network.
DHCP (Dynamic Host Configuration Protocol):DHCP automatically assigns IP addresses to devices on a network, simplifying the configuration process for users and administrators.
DNS (Domain Name System):DNS translates human-readable domain names into IP addresses, allowing users to access websites using easy-to-remember names.
FTP (File Transfer Protocol):FTP facilitates the transfer of files between computers on a network. It provides a reliable method for uploading and downloading files.
SMTP (Simple Mail Transfer Protocol):SMTP is a protocol used for sending emails. It defines how emails are transmitted from the sender's server to the recipient's server.
D. Cloud Computing:
Cloud computing involves delivering computing services (e.g., storage, processing power, applications) over the internet.
Infrastructure as a Service (IaaS):IaaS provides virtualized computing resources, including servers, storage, and networking, allowing users to build and manage their infrastructure.
Platform as a Service (PaaS):PaaS offers a platform that allows users to develop, run, and manage applications without dealing with the complexities of underlying infrastructure.
Software as a Service (SaaS):SaaS delivers software applications over the internet. Users can access and use the software without worrying about installation, maintenance, or updates.
E. Network Security Protocols:
Security protocols are essential for protecting data and ensuring the integrity and confidentiality of network communications.
SSL/TLS (Secure Sockets Layer/Transport Layer Security):SSL and its successor TLS are cryptographic protocols that provide secure communication over a computer network. They are commonly used in securing web traffic.
IPsec (Internet Protocol Security):IPsec is a suite of protocols that encrypts and authenticates data at the IP layer. It is often used in VPNs to secure communication over untrusted networks.
Firewall Rules:Firewalls enforce rules to control incoming and outgoing network traffic. They can be configured to allow or block specific data packets based on predefined security policies.
These above explained additional components and concepts expands the comprehension of the intricate nature of computer networks. As technology evolves, these components continue to play vital roles in building robust, secure, and efficient networks.





No comments:
Post a Comment